Palo Alto Ips
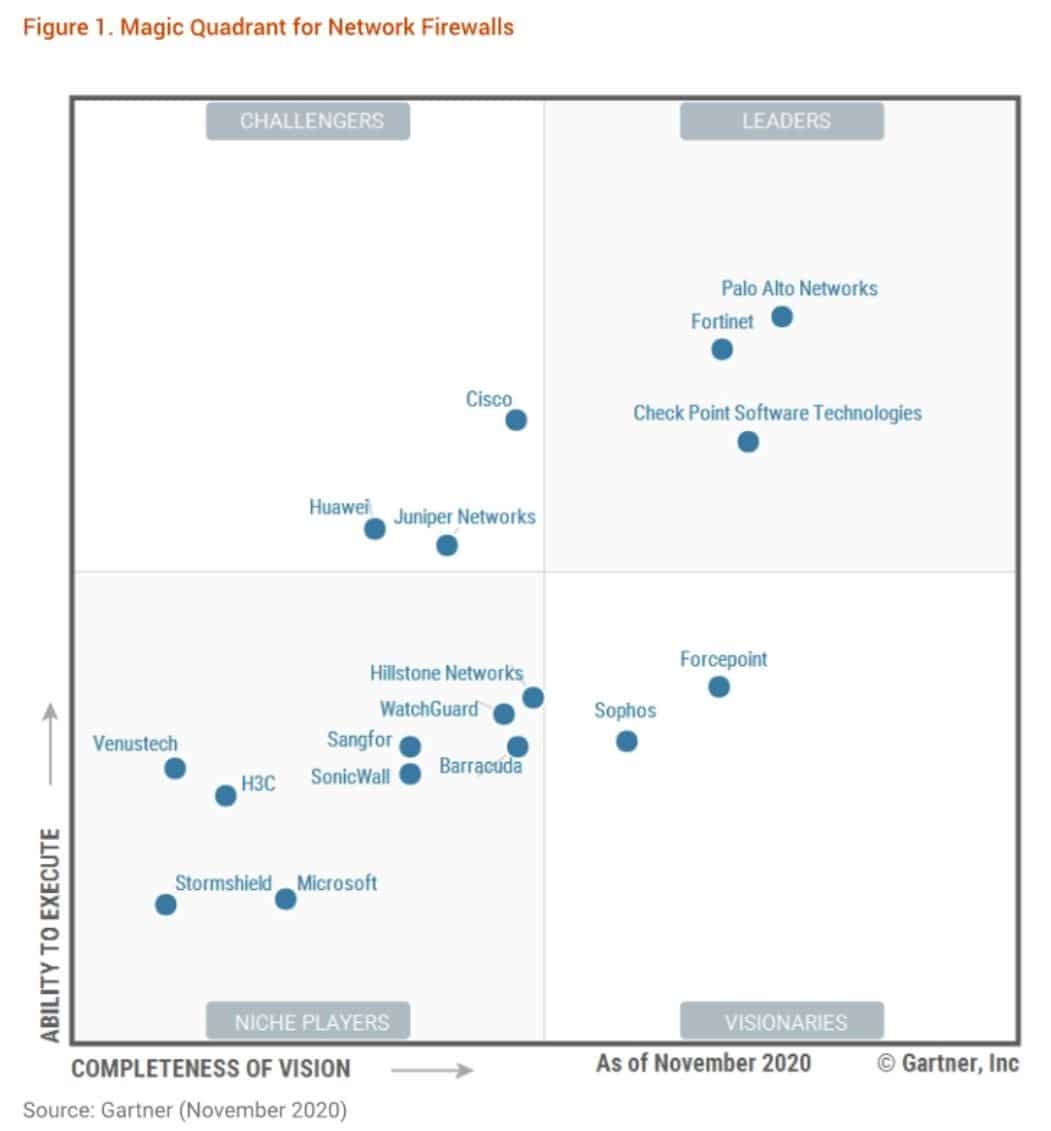
Palo Alto Networks Magic Quadrant Leader Enterprise Networks Solutions

Firewall Orange Cyberdefense Belgium
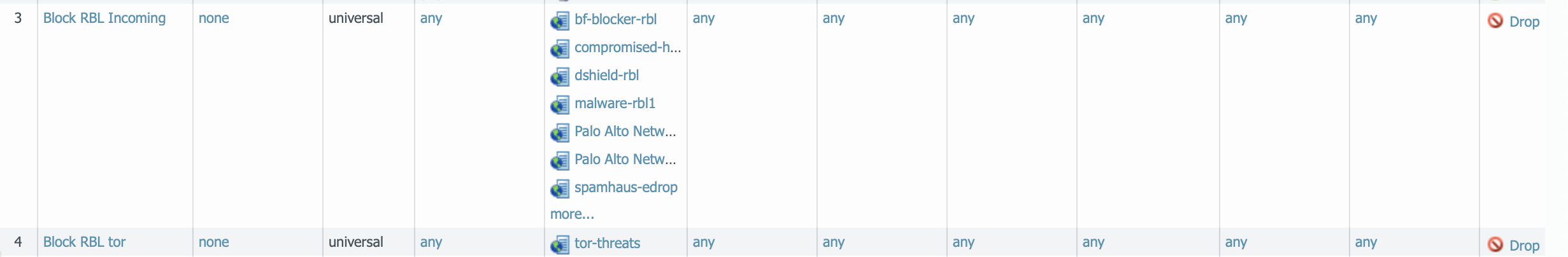
Adding Rbls To Your Paloalto Networks Firewall Dev Ops Docs

Aws Marketplace Threat Detection

Let S Learn Palo Alto Ngfw A Case Study Of Checkpoint Juniper Cisco Hacking And Knowing Thyself John Francis Joe Antony Sebastin Amazon Com Books
Www Infoblox Com Wp Content Uploads Infoblox Deployment Guide Infoblox Nios Integration With Palo Alto Networks Firewall Pdf
Palo Alto Networks Joins the Responsible Business Alliance By Jeff Rangel January 26, 21 at 10 PM 2 min read 2 MustRead Articles, Products and Services How Your Security Operations Team Can Maintain Zero Trust By Mark Brozek January 26, 21.
Palo alto ips. Key attributes of Palo Alto Networks next generation firewall • Designed to be a primary firewall, identifying and controlling applications users and content traversing the network • AppID Identifies and controls more than 900 applications of all types, irrespective of port, protocol, SSL encryption or evasive tactic. If clients choose to disclose diagnosis details, however, IPS job developers will provide support by working with the client and employer at the job site VAPAHCS is a mentor program for the national IPS Program (formerly Supported Employment) created under Public Law Eligibility. Palo Alto Networks ® Security Operating Platformの一環として専用に開発されたThreat Preventionサービスは、業界トップのIPS、ネットワーク アンチマルウェア、およびコマンドアンドコントロール(C2)の防御を使用して、攻撃ライフサイクル全体にわたってネットワークを.
Where I work, I have access to a couple of guys who are very IDS / IPS specialized from a research perspective and they like to do testing on evasion techniques, etc so while the Security Onion distro is certainly appealing (and I may be leveraging it for other functions), I. Recommended GlobalProtect App 50x or above releases Platform Supported Windows, Windows UWP, Mac, iOS, and Linux Both IPv4 and IPv6. Click on edit icon inside the Management Interface window Add the IP address or network address along with the subnet mask Commit the changes.
Where I work, I have access to a couple of guys who are very IDS / IPS specialized from a research perspective and they like to do testing on evasion techniques, etc so while the Security Onion distro is certainly appealing (and I may be leveraging it for other functions), I. IDS/IPS Solutions Home / Products / IDS/IPS Solutions / Palo Alto Networks IDS/IPS Solution NextGeneration Security Platform – Firewalls, Endpoint, Threat Prevention. To get started with converting IPS rules to custom threat signatures, download and install the IPS Signature Converter on Panorama If you have a Panorama HA configuration, repeat the installation process on each Panorama peer When installing the plugin on Panoramas in an HA pair, install the plugin on the passive peer before the active peer.
Note1 In a Palo Alto Networks firewall, you can create objects for IP addresses, Subnets etc For this you need to go to Objects>Addresses and create the object then refer it under interface or security/nat policy but on this post, I wrote IP addresses directly without any objects. I'm guessing that while great as a firewall, Palo Alto isn't primetime yet when it comes to being a dedicated IPS?. The Palo Alto Networks Network Device Management STIG is used for the configuration of the Palo Alto Networks device management functions, while either the Palo Alto Networks Application Layer Gateway STIG or the Palo Alto Networks Intrusion Detection and Prevention System STIG is used for the configuration of the device, depending on which.
Palo Alto VM Series is a firewall that makes up part of our security solution, handing IPS, IDS, and other security measures Pros and Cons "The most valuable features are web control and IPS/IDS". The Palo Alto Networks™ VMSeries extends secure application enablement into virtualised environments while addressing key virtualisation security challenges tracking security policies to virtual machine movement with dynamic address objects and integration with orchestration systems using a powerful XML management API. Performance Palo Alto topped all firewalls tested by NSS Labs with 7,8 Mbps performance, while Cisco posted a solid 5,291 Mbps Notably, NSS rated the performance of both devices lower than the.
弊社のIPSテクノロジは、専門のリサーチャーとシグネチャ開発者でサポートされています。弊社のチームは、脅威防御コミュニティで活躍しており、Microsoft Active Protections Program (MAPP)などのプログラムを通じて、公式非公式を問わず、ソフトウェア ベンダら. Passive DNS Monitoring Enable Telemetry Custom Signatures Threat Signature Categories (Snort is a free and open source IPS) Creating Custom Threat and Application Signatures—Walks through custom signature examples,. Palo Alto Networks will provide two lists of IP addresses to customers delivered as content to be used in External Dynamic Lists based on information from our threat intelligence Known malicious IP addresses This list includes malicious IP addresses that are currently used almost exclusively by malicious actors for malware distribution.
If clients choose to disclose diagnosis details, however, IPS job developers will provide support by working with the client and employer at the job site VAPAHCS is a mentor program for the national IPS Program (formerly Supported Employment) created under Public Law Eligibility. Palo Alto Networks differs from traditional Intrusion Prevention Systems (IPS) by bringing together vulnerability protection, network antimalware and antispyware into one service that scans all traffic for threats – all ports, protocols and encrypted traffic. Click on edit icon inside the Management Interface window Add the IP address or network address along with the subnet mask Commit the changes.
The Palo Alto Networks security platform is a “thirdgeneration” or “nextgeneration” firewall These devices are capable of inspecting the entire packet, including the payload, and making a forwarding decision based on configured policies. •Simplified Policy ManagementPalo Alto Networks application, user and content control policies are implemented from a single, centralized policy table whereas IPS management is typically cumbersome, requiring multiple interfaces to implement a security policy. Update your Palo Alto appliance By default, Palo Alto deploys 800 for the 80X series and 810 for the 81X series In this case, Palo Alto will strongly recommend you upgrade the appliance to the latest version of that series before helping you with support cases.
9 By Stephen Perciballi September 28, 15 at 100 PM. I'm guessing that while great as a firewall, Palo Alto isn't primetime yet when it comes to being a dedicated IPS?. Whitelist Vendor IP range from Paloalto IPS Hi All, I am looking for more effective way to whitelist a vendor on IPS without whitelisting at the FW as well I am looking for traffic from vendore ip range to be completely exempted from Vulnerability / antivirus / Antispyware without creating any firewall rule and security profile.
The Palo Alto Networks MSSP Program offers two levels of membership to Service Providers who want to partner with Palo Alto Networks When you become a Palo Alto Networks MSSP program member, Palo Alto Networks commits the time and resources needed to help you differentiate your organization as a total solution provider for security services. 弊社のIPSテクノロジは、専門のリサーチャーとシグネチャ開発者でサポートされています。弊社のチームは、脅威防御コミュニティで活躍しており、Microsoft Active Protections Program (MAPP)などのプログラムを通じて、公式非公式を問わず、ソフトウェア ベンダら. Palo Alto Networks is able to identify attacks driven by LOIC, Trinoo and others and automatically block their DDoS traffic at the firewall.
Palo Alto Networks nextgeneration firewalls give you the ability to safely enable access to Office 365 with appropriate control With the latest AppID enhancements, you can Enable access to Enterprise Office 365 account types while blocking access to Consumer account types. If you like my free course on Udemy including the URLs to download images All I ask is a 5 star rating!https//wwwudemycom/paloaltofirewallsinstallatio. < 9012 on P, PA800, PA3000 Series, PA30 Series, PA50 Series, P000 Series.
The Palo Alto Networks firewall is a stateful firewall, meaning all traffic passing through the firewall is matched against a session and each session is then matched against a security policy A session consists of two flows The Client to Server flow (c2s flow) and the Server to Client flow (s2c flow). I'm guessing that while great as a firewall, Palo Alto isn't primetime yet when it comes to being a dedicated IPS?. Share Threat Intelligence with Palo Alto Networks What Telemetry Data Does the Firewall Collect?.
Palo Alto Network NextGeneration Firewall and GlobalProtect App with PANOS 81 or above To use Address Group, PANOS 90 or above;. Palo Alto Networks Threat Prevention goes beyond typical intrusion prevention system (IPS) to inspect all traffic for threats, regardless of port, protocol or encryption and automatically blocks known vulnerabilities, malware, exploits, spyware, and commandandcontrol Customers can import, sanitize, manage and completely automate workflows to rapidly apply IPS signatures in popular formats. 弊社のIPSテクノロジは、専門のリサーチャーとシグネチャ開発者でサポートされています。弊社のチームは、脅威防御コミュニティで活躍しており、Microsoft Active Protections Program (MAPP)などのプログラムを通じて、公式非公式を問わず、ソフトウェア ベンダら.
< 9012 on P, PA800, PA3000 Series, PA30 Series, PA50 Series, P000 Series. < 9012 on P, PA800, PA3000 Series, PA30 Series, PA50 Series, P000 Series. The Palo Alto Networks® nextgeneration firewall protects and defends your network from commodity threats and advanced persistent threats (APTs) The multipronged detection mechanisms of the firewall include a signaturebased (IPS/Command and Control/Antivirus) approach, heuristicsbased (bot detection) approach, sandboxbased (WildFire.
Recommended GlobalProtect App 50x or above releases Platform Supported Windows, Windows UWP, Mac, iOS, and Linux Both IPv4 and IPv6. Palo Alto Networks security platform components, including sensors, event databases, and management consoles must integrate with a networkwide monitoring capability An integrated, networkwide intrusion detection capability increases the ability to detect and prevent sophisticated distributed attacks based on access patterns and. 18 NSS Labs Recommended NGIPS UNPARALLELED PROTECTION FROM PALO ALTO NETWORKS We’ve earned another Recommended rating for the 18 NSS Labs Next Generation Intrusion Prevention System (NGIPS) Group Test NSS Labs® has published the results of its 18 Next Generation Intrusion Prevention System (NGIPS) Test Report and Security Value Map™.
For Palo Alto Networks (CIS Palo Alto Firewall 9 Benchmark version 100) Complete CIS Benchmark Archive CIS Covers Other Server Technologies See the full list Information Hub CIS Palo Alto Networks Benchmarks Webinar • 05 Feb 21 OnDemand Webinar How to Secure Your Cloud with CIS. Palo Alto Networks nextgeneration firewalls arm you with a twopronged approach to stopping these attacks Unwanted applications are blocked through AppID, and the applications you choose to allow through are scanned for vulnerability exploits by our NSSapproved IPS engine. Palo Alto Networks’ nextgeneration firewalls with IPS capabilities arm you with a proven approach to stopping these attacks Vulnerability exploits, buffer overflows, port scans, and exploit kits are detected and stopped using signatures, heuristics, and statistical anomaly detection.
The Palo Alto Networks® nextgeneration firewall protects and defends your network from commodity threats and advanced persistent threats (APTs) The multipronged detection mechanisms of the firewall include a signaturebased (IPS/Command and Control/Antivirus) approach, heuristicsbased (bot detection) approach, sandboxbased (WildFire. Palo Alto Networks Prisma Cloud Compute customers can enable those mitigations through the builtin Admission support for OPA rules Please refer to the “Prisma Cloud Compute Mitigation” section for instructions The Vulnerability CVE8554 stems from a design flaw in two features of Kubernetes Services External IPs and Load Balancer IPs. The Palo Alto Networks™ VMSeries extends secure application enablement into virtualised environments while addressing key virtualisation security challenges tracking security policies to virtual machine movement with dynamic address objects and integration with orchestration systems using a powerful XML management API.
The following table lists all possible signature categories by type—Antivirus, Spyware, and Vulnerability—and includes the content update (Applications and Threats, Antivirus, or WildFire) that provides the signatures in each category You can also go to the Palo Alto Networks Threat Vault to Learn More About Threat Signatures. < 9012 on P, PA800, PA3000 Series, PA30 Series, PA50 Series, P000 Series. Palo Alto Firewall URL Filtering Resolution Many of you are wondering, “How do I test to see if our URL Filtering service is enforcing my organization’s policies for malicious and benign URLs properly?”.
Create a different QoS profiles using the same class Check the figure below. Additional IPS reports for Palo Alto Networks firewalls mrichardson03/panosipsreports. The following document describes how to allow certain IP addresses to access the Management Interface on the Palo Alto Networks firewall Steps From the WebGUI Go to Device > Setup > Management tab;.
The firewall displays only the logs you have permission to see For example, if your administrative account does not have permission to view WildFire Submissions logs, the firewall does not display that log type when you access the logs pages. The following document describes how to allow certain IP addresses to access the Management Interface on the Palo Alto Networks firewall Steps From the WebGUI Go to Device > Setup > Management tab;. Deep packet inspection is a methodology that network security professionals have been doing for many years It involves looking at the data going over the network and determining if anything malicious is going on based on what's in those packets When I was cutting my teeth on Solaris back in the late 90's, we used snoop 1 to grab a packet capture to troubleshoot issues.
PolicyBased Forwarding (Palo Alto Networks firewall connection to a different firewall vendor) This method can be used when the connection is between two firewalls State from what Source Zone Indicate when the traffic is destined to the network on the other side of the tunnel (in this case it is /24) Forward the traffic down the. Palo Alto Firewall QoS Configuration Resolution Case 1 Limiting uploads This is only applicable when the Firewall is not performing NAT operation There are multiple subnets behind the LAN interface for which we have to limit the upload to ;. The Future of Intrusion Prevention Why Your Next IPS is a NextGeneration Firewall August 10 Palo Alto Networks 232 E Java Drive Sunnyvale, CA 940.
PolicyBased Forwarding (Palo Alto Networks firewall connection to a different firewall vendor) This method can be used when the connection is between two firewalls State from what Source Zone Indicate when the traffic is destined to the network on the other side of the tunnel (in this case it is /24) Forward the traffic down the. An Intrusion Prevention System (IPS) is a network security/threat prevention technology that examines network traffic flows to detect and prevent vulnerability exploitsVulnerability exploits usually come in the form of malicious inputs to a target application or service that attackers use to interrupt and gain control of an application or machine. Where I work, I have access to a couple of guys who are very IDS / IPS specialized from a research perspective and they like to do testing on evasion techniques, etc so while the Security Onion distro is certainly appealing (and I may be leveraging it for other functions), I.
Network IPS Tuning Guide Threat Prevention Cyber Kill Chain intrusion prevention systems IPS Network intrusion prevention systems Network IPS VPN 16,967 people reacted;. Deep packet inspection is a methodology that network security professionals have been doing for many years It involves looking at the data going over the network and determining if anything malicious is going on based on what's in those packets When I was cutting my teeth on Solaris back in the late 90's, we used snoop 1 to grab a packet capture to troubleshoot issues. An Intrusion Detection System (IDS) is a network security technology originally built for detecting vulnerability exploits against a target application or computerIntrusion Prevention Systems (IPS) extended IDS solutions by adding the ability to block threats in addition to detecting them and has become the dominant deployment option for IDS/IPS technologies.
VA Palo Alto Health Care System Individual Placement and Support (CWT/IPS) The Individual Placement and Support Program provides competitive placement with onsite support services for participants with a diagnosis of severe mental illness (SMI). Palo Alto Networks Joins the Responsible Business Alliance By Jeff Rangel January 26, 21 at 10 PM 2 min read 2 MustRead Articles, Products and Services How Your Security Operations Team Can Maintain Zero Trust By Mark Brozek January 26, 21. Palo Alto is an application firewall (Do not confuse it with web application firewalls) It cannot be compared with the ASA since the are not in the same category Palo Alto claims that it's firewall can inspect https traffic, control which application can or cannot use port 80 and 443, IPS,VPN etc So it does the same things with an ASA plus more.

Static Nat On Palo Alto A Team Chronicles
Palo Alto Networks Firewall Security Logging

Palo Alto Networks Ngfw Firecompass
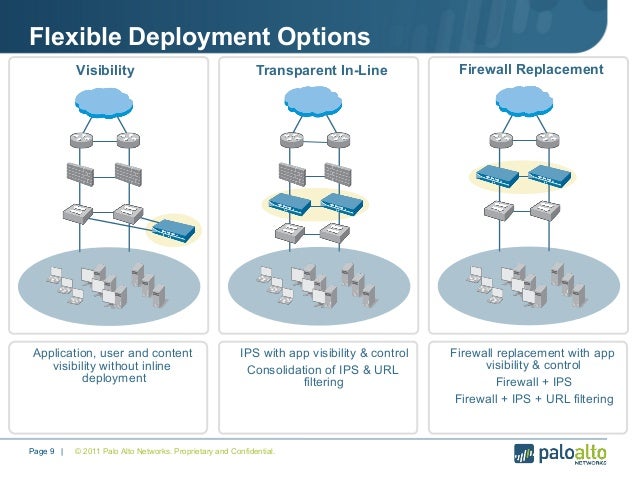
Palo Alto Networks Y La Tecnologia De Next Generation Firewall

Configure Palo Alto And Qradar To Automatically Block Bad Ips Part 4 Youtube

Vrealize Network Insight Nsx And Palo Alto Networks For Micro Segmentation Network And Security Virtualization Vmware
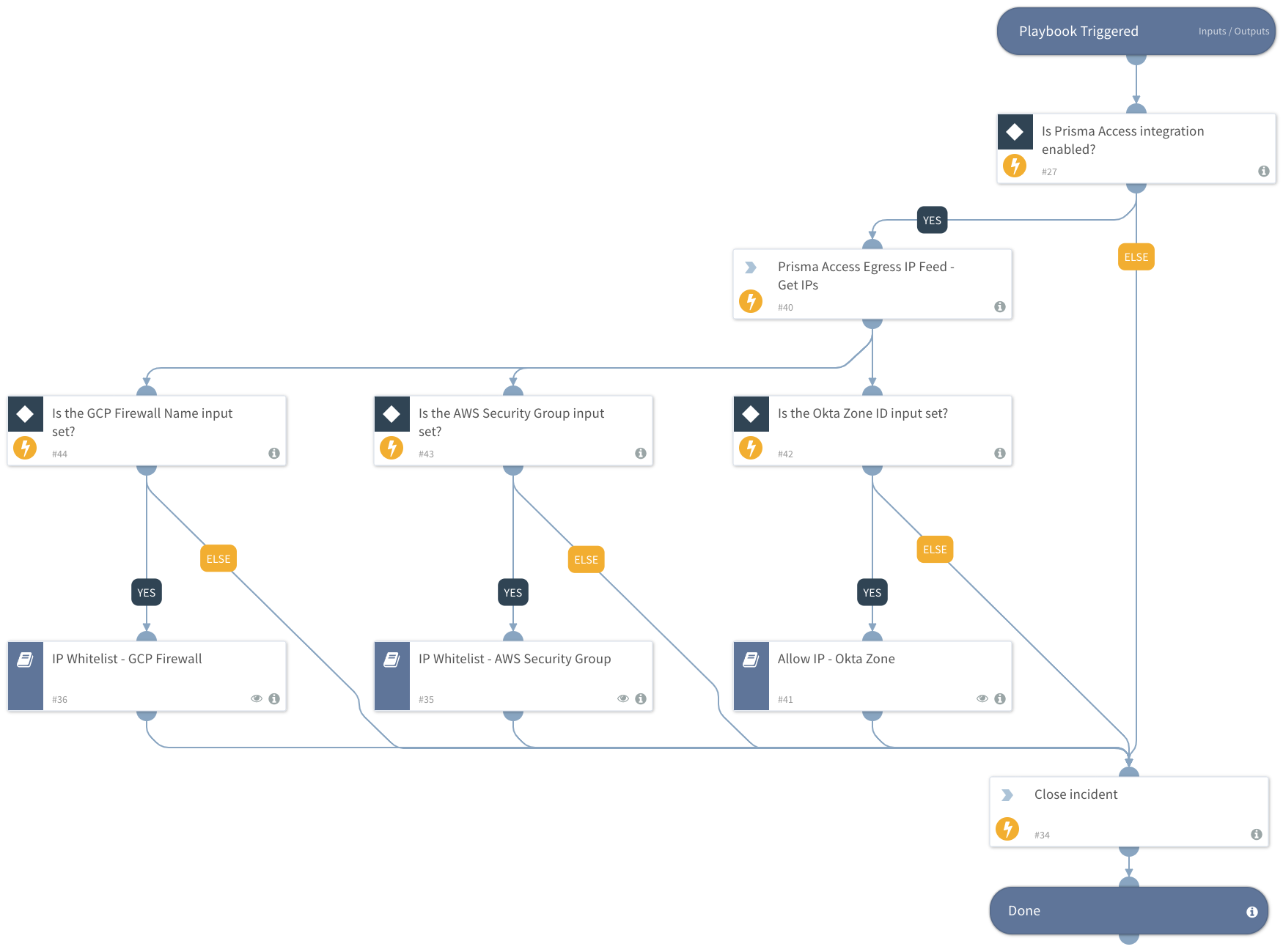
Prisma Access Whitelist Egress Ips On Saas Services Cortex Xsoar
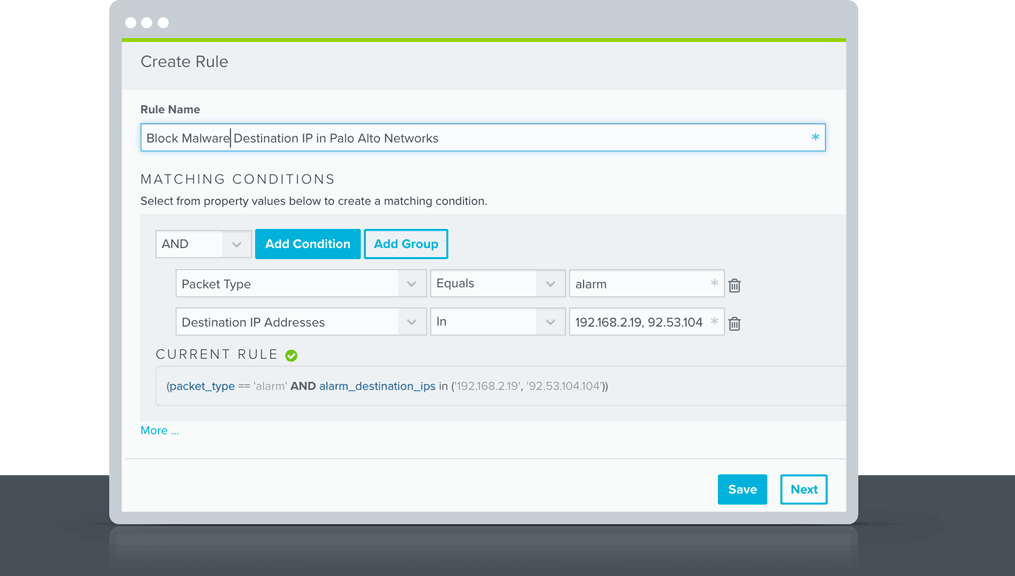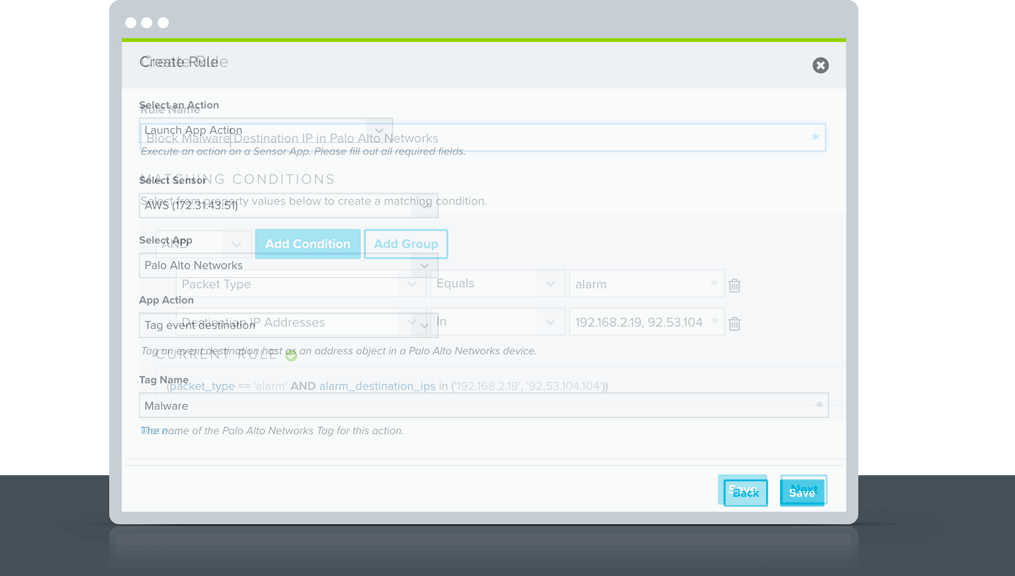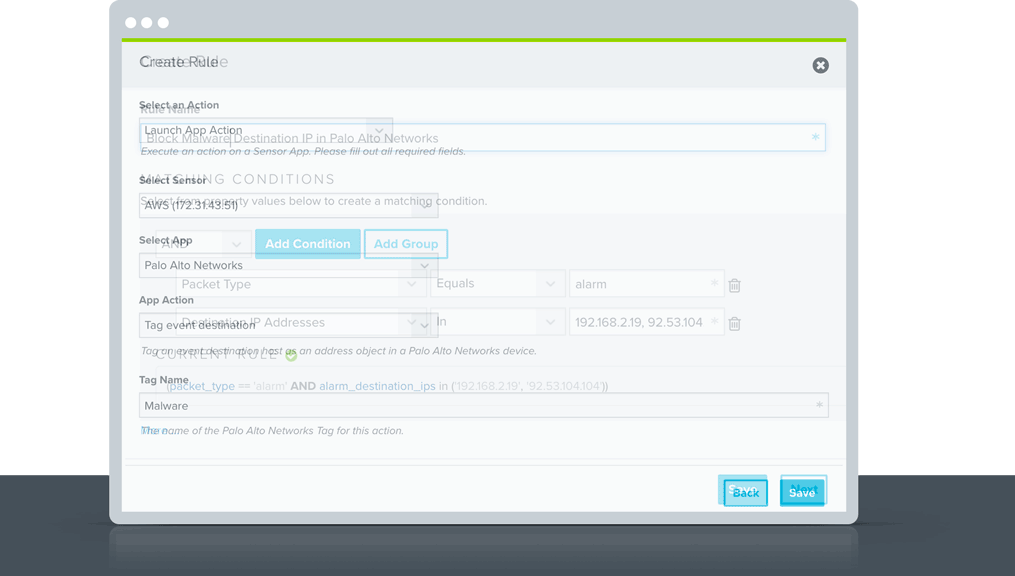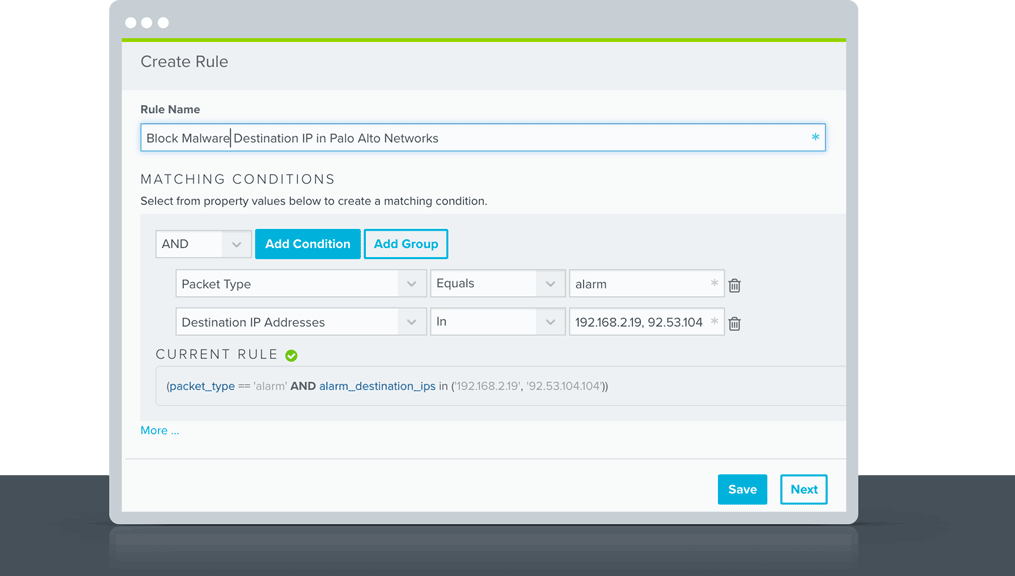
Alienapp For Palo Alto Networks Alienvault

Palo Alto Firewall And Bgp Routing David Vassallo S Blog

Palo Alto Redlock And Public Cloud Threat Defense Marius Sandbu
Learning By Practicing Building A Monitoring Solution Forwarding Palo Alto Logs

Palo Alto Convergys Shares Rise On Acquisitions Marketwatch
Www Skyboxsecurity Com Wp Content Uploads 03 Skybox Tb Paloalto Networks Pdf

Cisco Asa Firepower Vs Palo Alto Firewall Cisco Sourcefire Vs Palo Alto Wildfire
How To Add Exempt Ip Addresses From The Threat Monitor Logs Knowledge Base Palo Alto Networks
Andres Cardenal Blog Palo Alto Networks A Growth Leader In Cybersecurity Talkmarkets
Www F5 Com Pdf Partners F5 Big Ip Platform Palo Alto Networks Next Gen Firewall Solution Pdf

Aws Transit Vpc Part 2 With Palo Alto Networks And Vmware Cloud On Aws

Aci Security Part 1

Finding Hidden Meaning In Your Palo Alto Networks Ips Ids Deployments

Palo Alto Networks Pa 800 Series Next Generation Manualzz

Palo Alto Interview Questions And Answers Part I Beginner S Forum
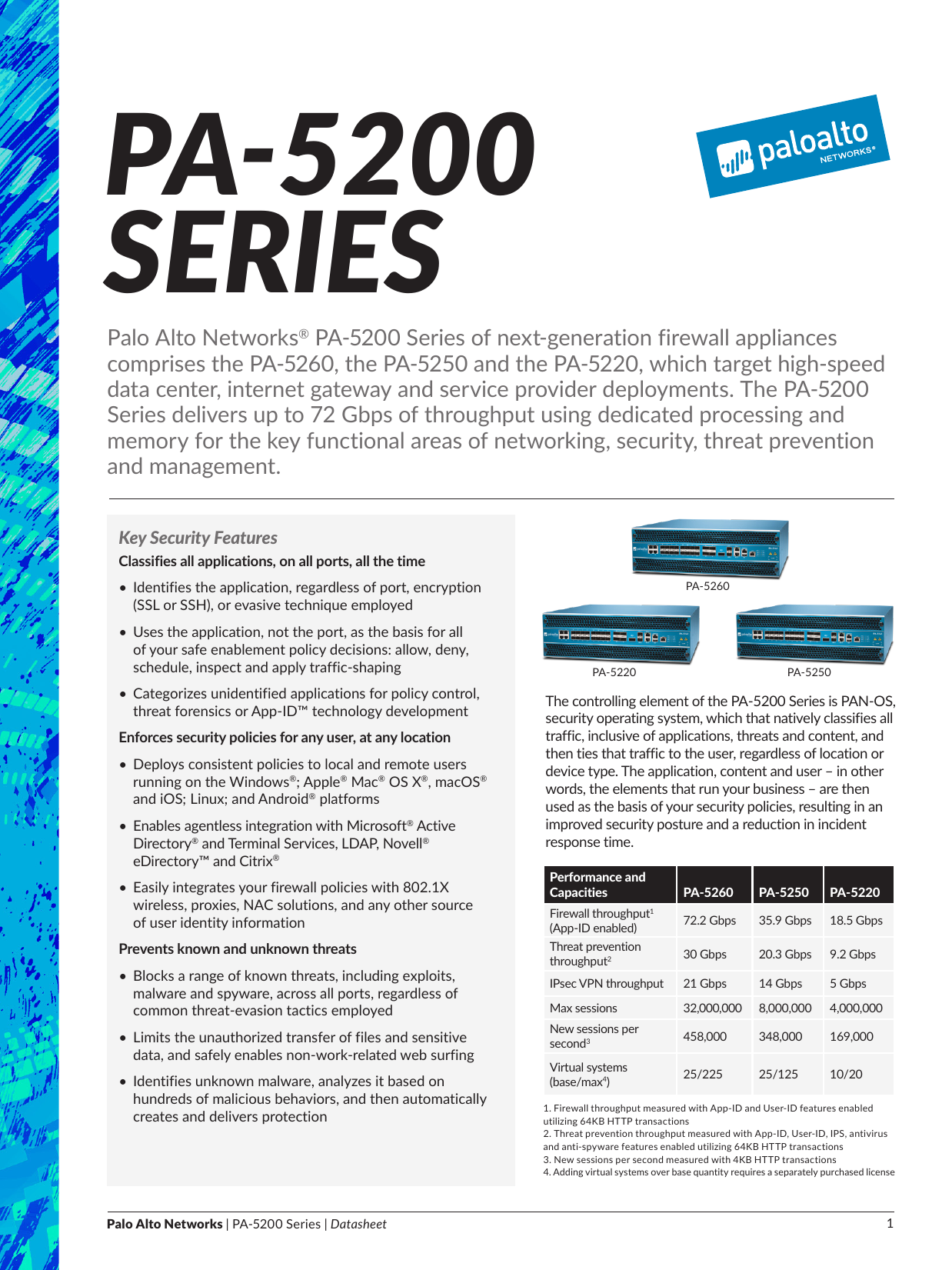
Palo Alto Networks Pa 50 Series Of Next Manualzz
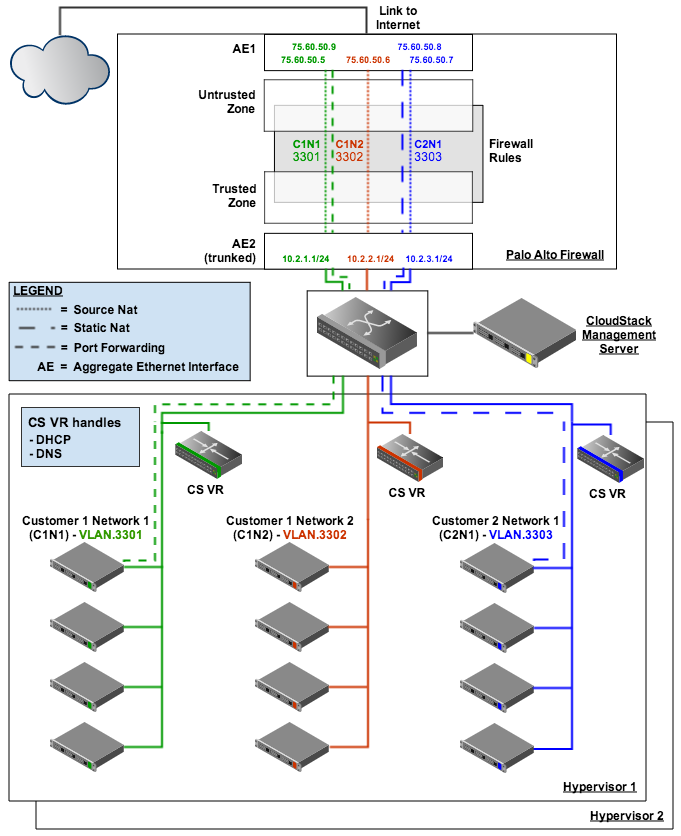
Cloudops Use A Palo Alto Networks Firewall With Cloudstack

Comparing Palo Alto Networks With Ips Products Exclusive Networks

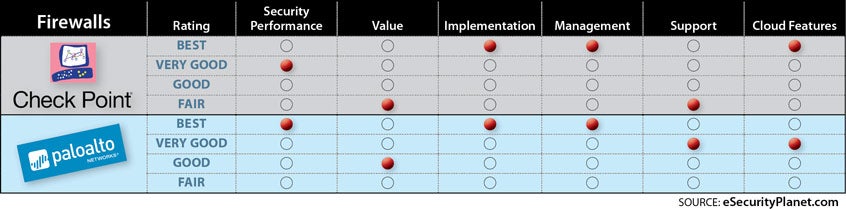
Check Point Ips Vs Palo Alto Networks Threat Prevention Comparison It Central Station

Setup Api Access To Palo Alto Networks Vm Series Aviatrix Docs Documentation
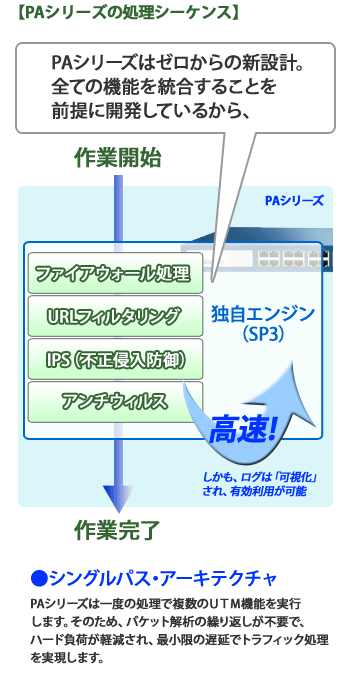
高性能utm Ips 製品情報 次世代ファイアウォール Palo Alto Networks Pa シリーズ 株式会社日立ソリューションズ
Firewall Hardening Best Practices For Palo Alto Networks
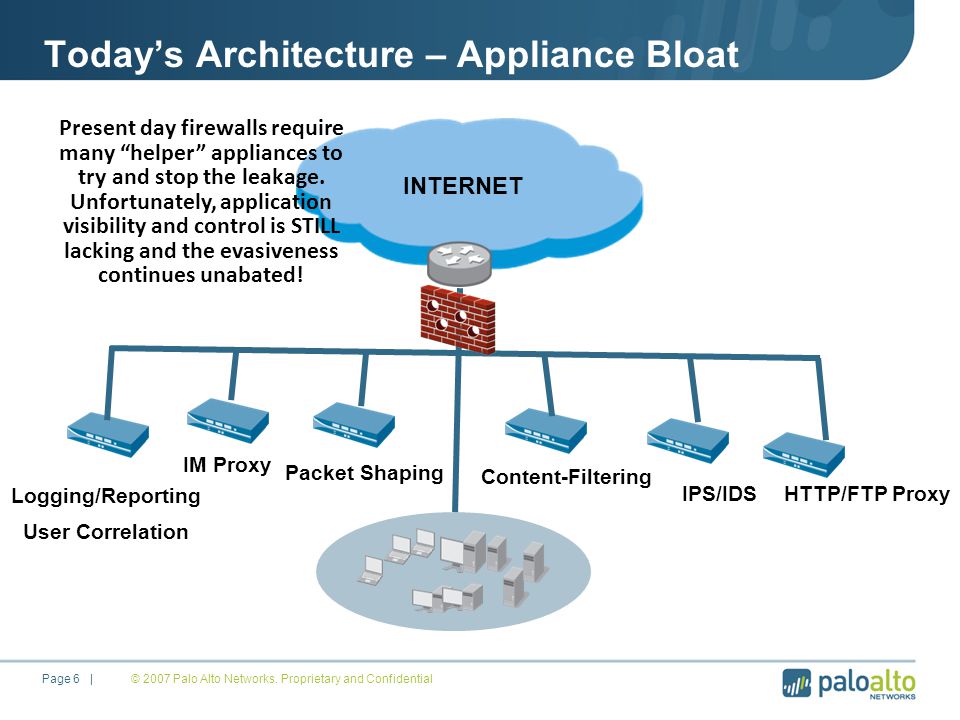
Applications Have Changed Why Hasn T The Firewall Dave Smith Von Nguyen Ppt Download
How To Block The Source Of A Threat For A Specific Time Interval Knowledge Base Palo Alto Networks
Github Azuregomez Paloalto Ha Hub Hub Vnet With Palo Alto Firewalls In Availability Set
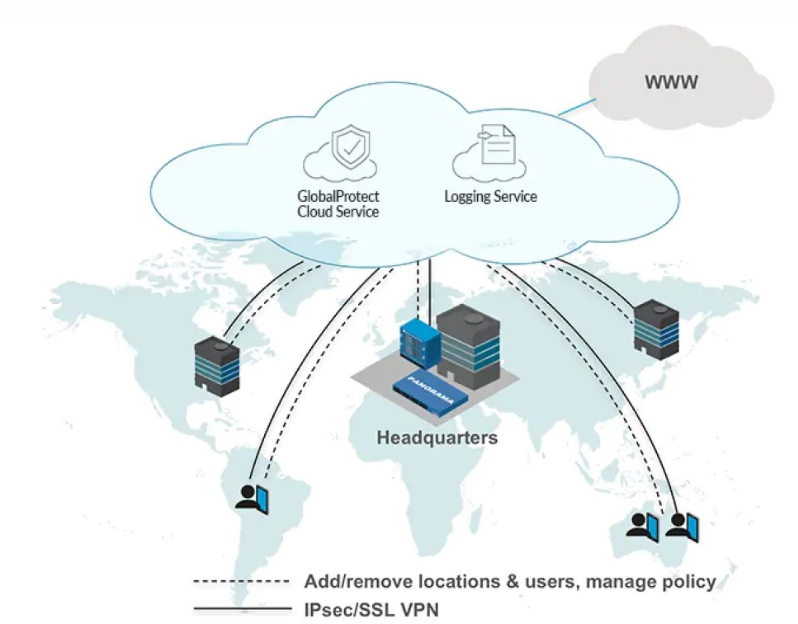
Palo Alto Integration By Using Ipsec Tunnels
Www Vmware Com Content Dam Digitalmarketing Vmware En Pdf Whitepaper Products Nsx Nsx Palo Alto Networks White Paper Pdf
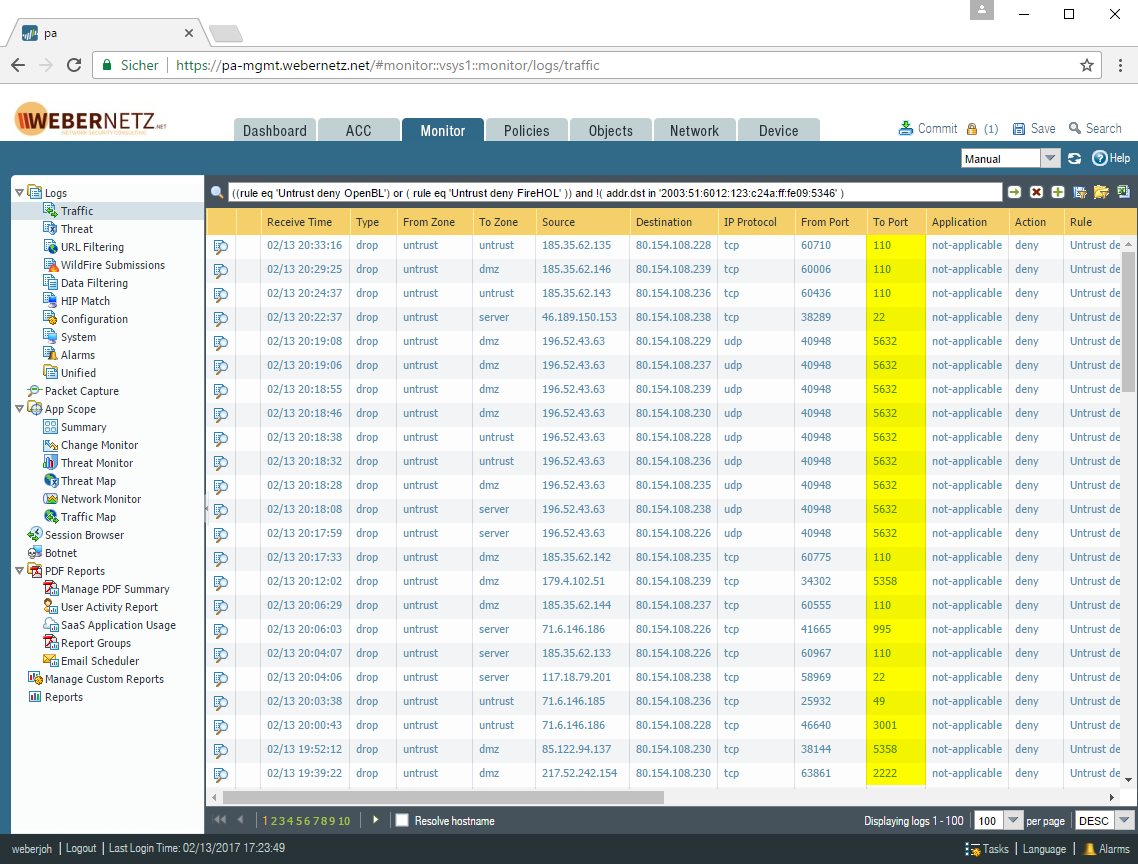
Palo Alto External Dynamic Ip Lists Weberblog Net

End To End Security With Palo Alto Networks Onur Kasap Engineer Pal
No Service Profile Found Error When Deploying The Vm Series With Panorama

Palo Alto Networks And Wdatp Ad Hoc Integration Microsoft Tech Community
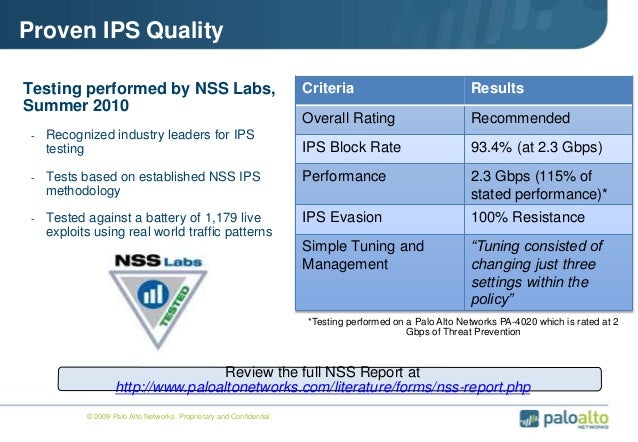
Www Stallion Ee Seminar Rigapan A Summary Of Ips Test Results And Core Capabilities Pdf

Palo Alto Networks Exclusive Networks Nederland
Role Based Admin Not Showing Full Ip Or Username In Logs And Re Knowledge Base Palo Alto Networks
Allowing Specific Ip Addresses To Access The Palo Alto Network Knowledge Base Palo Alto Networks

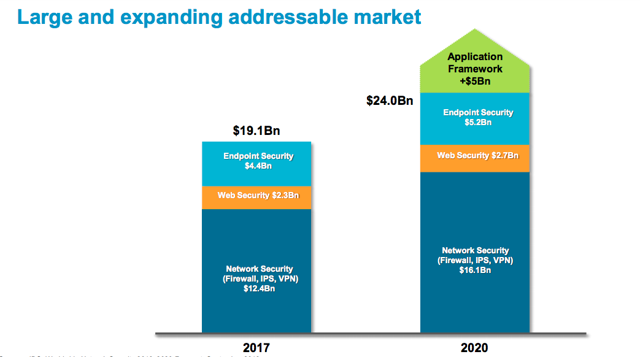
Palo Alto Networks Portfolio Strategy Overview 19

Firewalls Palo Alto Networks
Q Tbn And9gctxiztdutizp Dokytt4xil U4ilrllhkr5zsxwhlm Usqp Cau
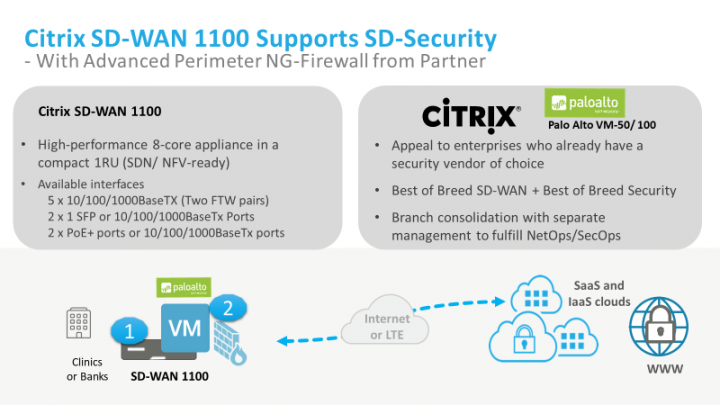
Citrix And Palo Alto Networks Team Up To Secure The Wan Edge Citrix Blogs
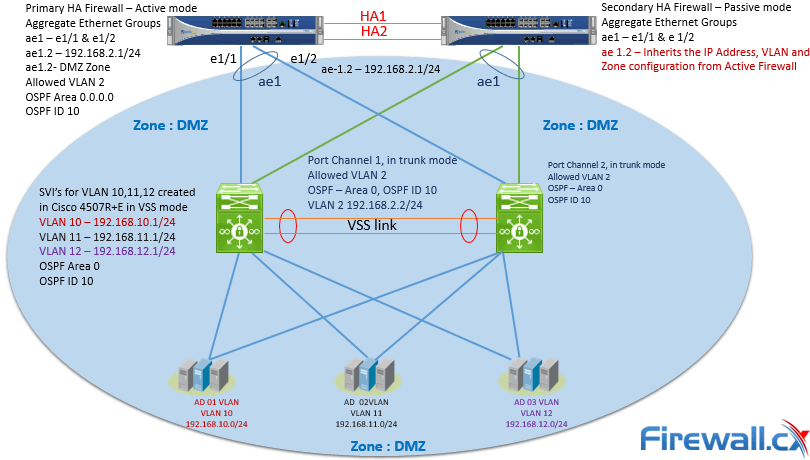
Palo Alto Firewalls Security Zones Tap Zone Virtual Wire Layer 2 And Layer 3 Zones
How To Determine The Number Of Threat Signatures On A Palo Alto Knowledge Base Palo Alto Networks

Palo Alto Networks Next Generation Firewall Virtual Netcomm Blog
How To Find Matching Signature For Vulnerabilities Knowledge Base Palo Alto Networks

Palo Alto Networks Security Solution Protection Against

Palo Alto Networks Pa 2 Brings Next Manualzz
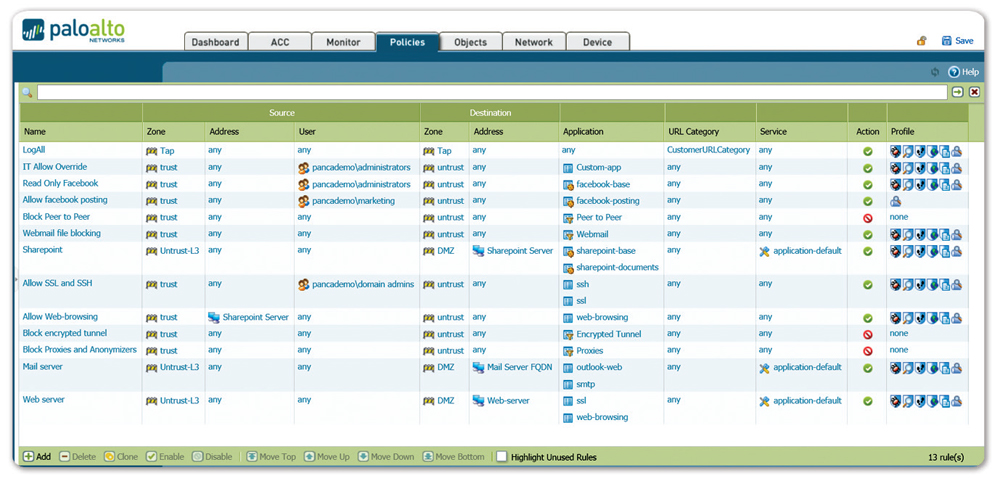
Palo Alto Networks Vm 100 מוצרי פאלו אלטו

Integrating Next Gen Firewalls With Vmware Cloud On Aws Aws Partner Network Apn Blog

Palo Alto Networks And Kentik Kentik

4 Palo Alto Networks Tools You Have To Discover
Check Point Vs Palo Alto Networks Top Ngfws Compared
Ppt Palo Alto Networks Overview Powerpoint Presentation Free Download Id

Waf Vs Ngfw
Upgrade Pan Os On A Standalone Palo Alto Firewall
Palo Alto Networks Just Another Firewall

Paloalto 8 0 1 Firewall High Availability Failover Youtube

Palo Alto Networks Pa 5000 Series Palo Alto Networks

Palo Alto Networks Komt Met Pa 7050 Computable Nl

Palo Alto Networks And Wdatp Ad Hoc Integration Microsoft Tech Community

Palo Alto Netowrks Ips Evasion Demo Nss Labs Youtube
Creating Customvulnerability Protection Rules For Palo Alto Networks Devices By Mehmet Afsin Guven Medium

Integrating Palo Alto With Logz Io S Cloud Siem Logz Io
Www Boll Ch Datasheets Pa 50 Series Pdf

Lessons Learned Palo Alto In Vwire Mode David Vassallo S Blog
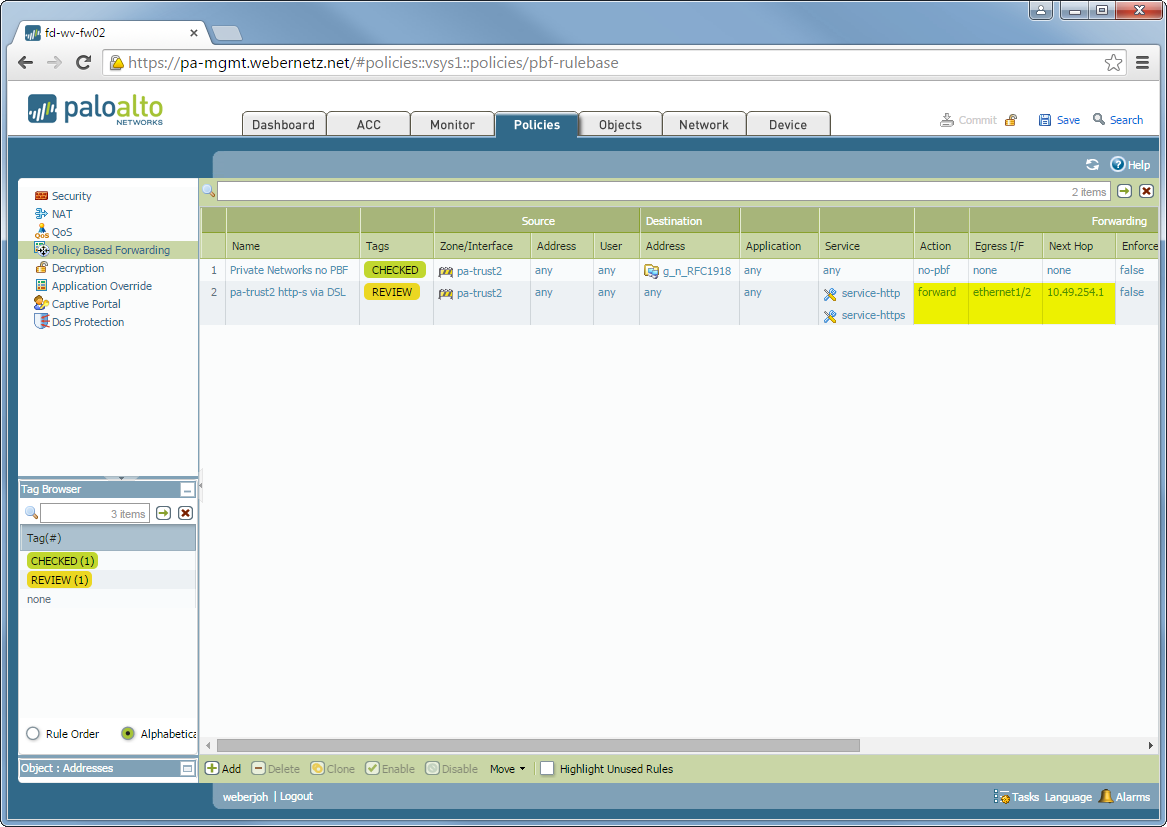
Policy Based Forwarding On A Palo Alto With Different Virtual Routers Weberblog Net

Palo Alto Vm Series Ha Deployment In Oci A Team Chronicles

Azure Sentinel Connector With Palo Alto Firewalls European Sharepoint Office 365 Azure Conference 21

Palo Alto Firewalls Security Profiles Anti Virus Spyware Ips Url Filtering Youtube
Paired Icon Registration Failing With Lifesize Cloud Nodes When Icon Is Behind Palo Alto Firewall
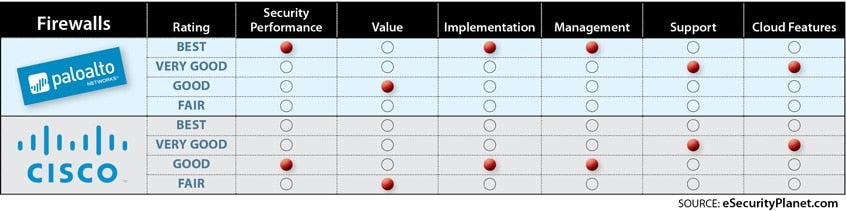
Cisco Vs Palo Alto Networks Top Ngfws Compared
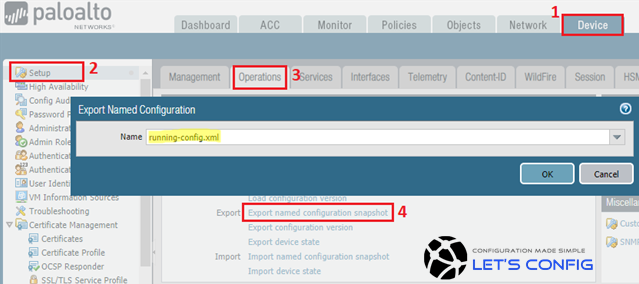
How To Save An Entire Configuration For Import Into Another Pal Knowledge Base Palo Alto Networks

Amendment No 3 To Form S 1
Www Vmware Com Content Dam Digitalmarketing Vmware En Pdf Whitepaper Products Nsx Nsx Palo Alto Networks White Paper Pdf

Palo Alto Networks App For Splunk Splunkbase
Www F5 Com Pdf Partners F5 Big Ip Platform Palo Alto Networks Next Gen Firewall Solution Pdf

Palo Alto Networks Ids Ips Solution Enterprise It Network Security Solutions By Giganetworks Putting The Value Back Into Value Added Reseller

Firewalls Palo Alto Networks
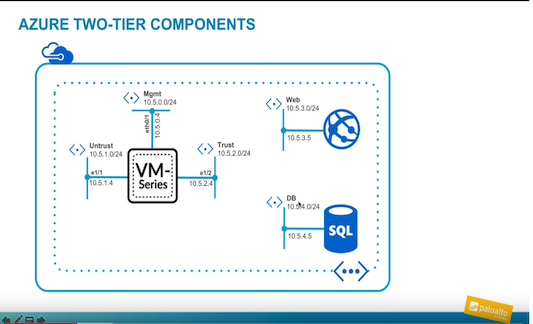
Vm Series Next Generation Firewall From Palo Alto Networks
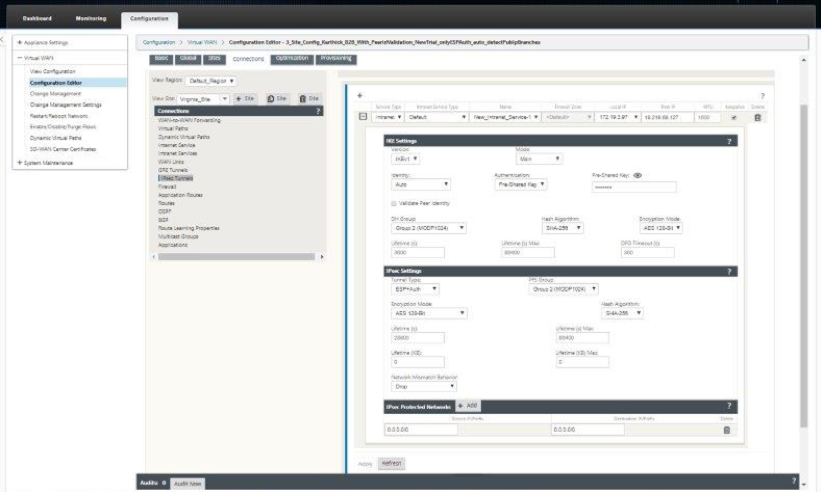
Palo Alto Integration By Using Ipsec Tunnels

End To End Security With Palo Alto Networks Onur Kasap Engineer Pal

Palo Alto Networks Vendors

Palo Alto Networks And Wdatp Ad Hoc Integration Microsoft Tech Community

Tips For Deploying Palo Alto Networks Vm Series Firewall With Vmware Nsx Wahl Network
How To Test Threat Prevention Using A Web Browser Knowledge Base Palo Alto Networks

Multi Site With Cross Vc Nsx And Palo Alto Networks Security Network And Security Virtualization Vmware
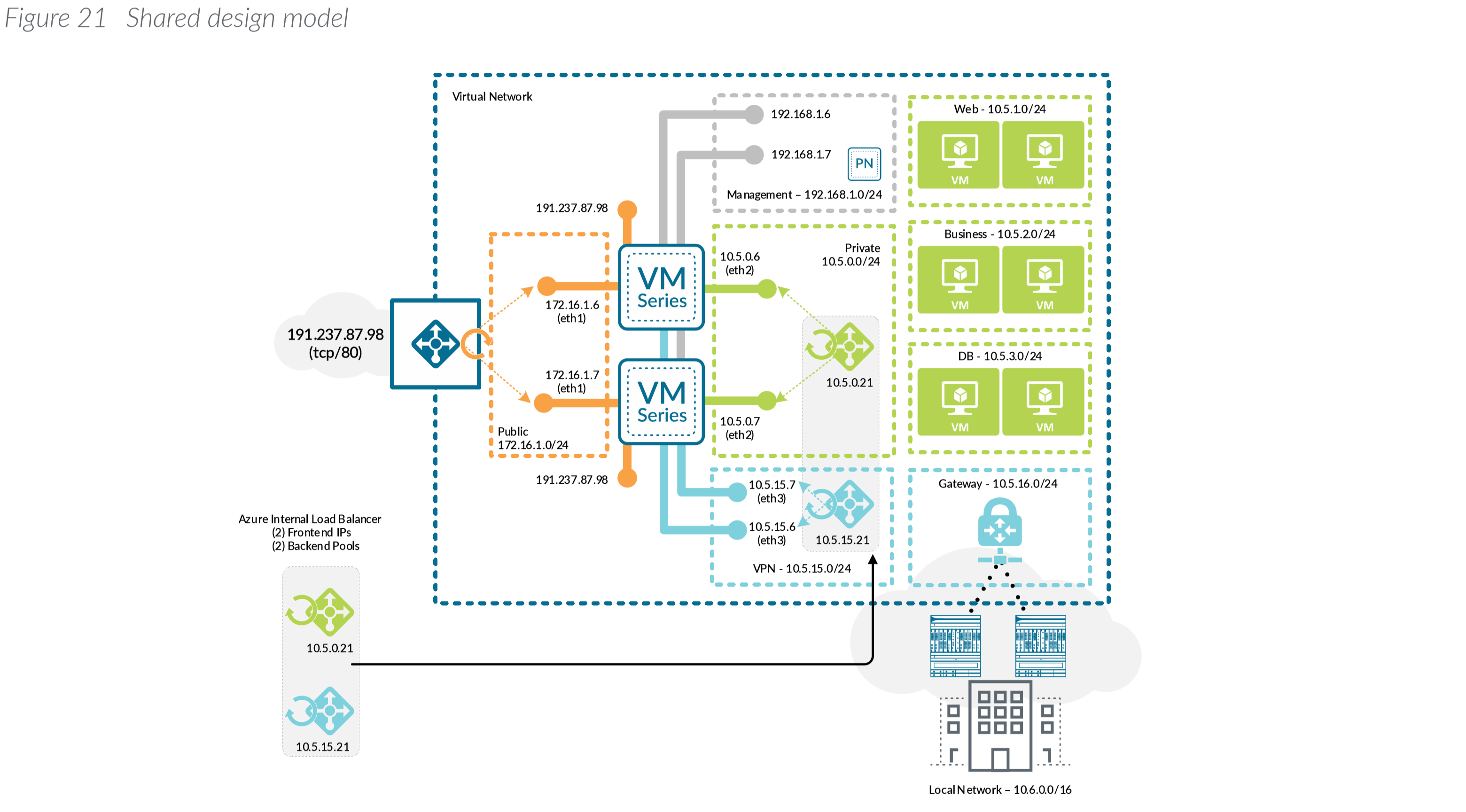
Deploying Palo Alto Vm Series On Azure Jack Stromberg
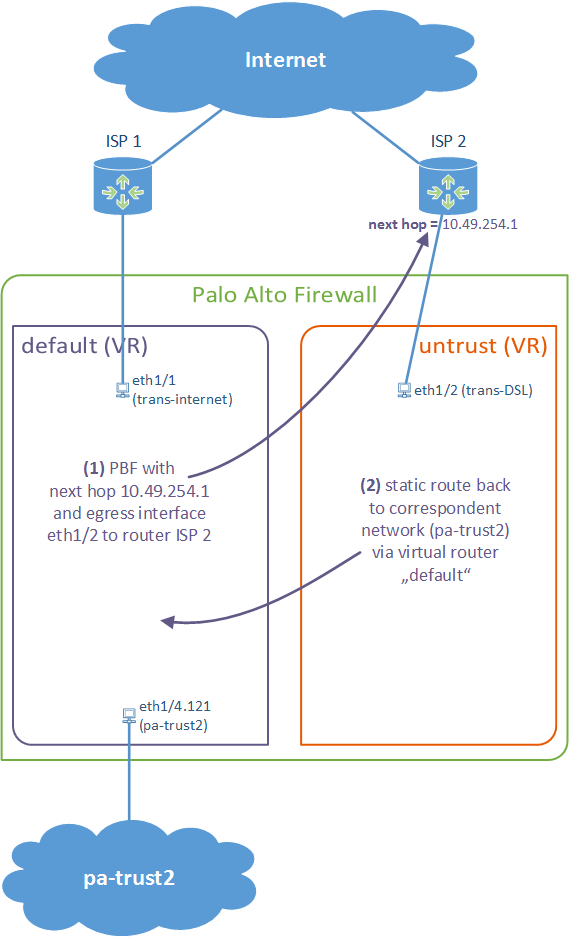
Policy Based Forwarding On A Palo Alto With Different Virtual Routers Weberblog Net
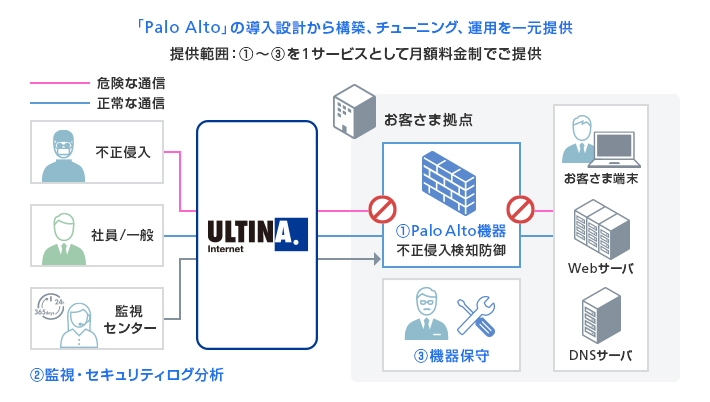
不正侵入検知防御サービス Palo Alto Networks Advance オプションサービス インターネット 法人のお客さま ソフトバンク

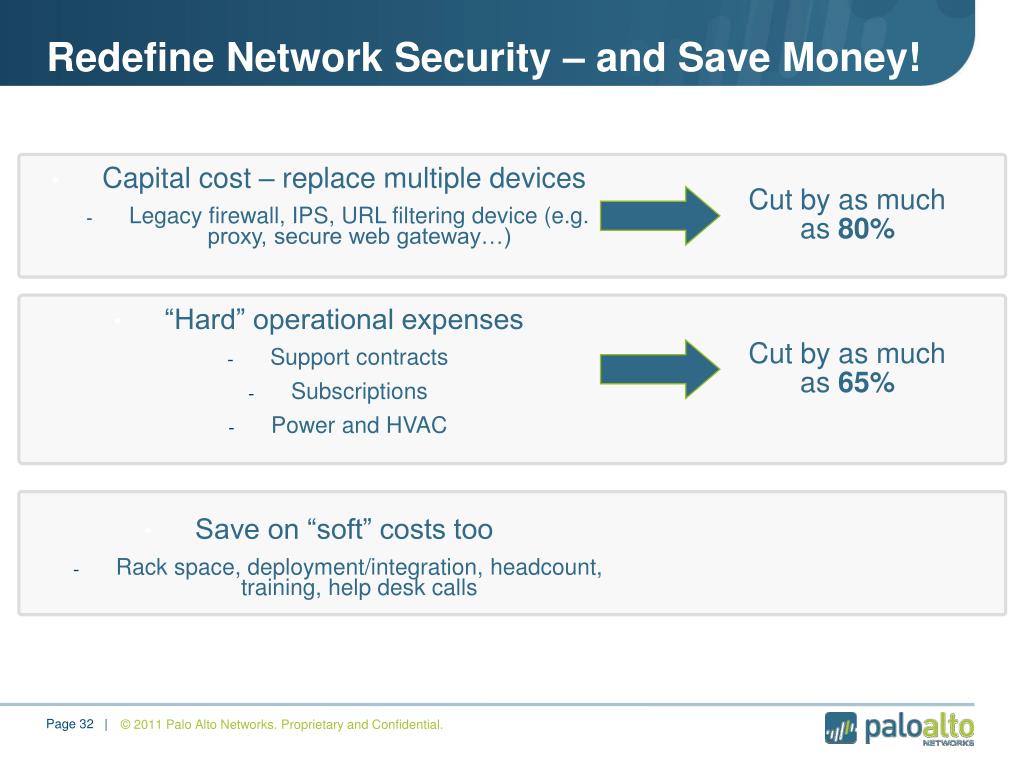
Palo Alto Networks Overview Ppt Video Online Download



